Understanding Security Terms
There are a lot of security terms out there and it can be hard to know which is which and what they all mean. Use this list of FAQs to learn more about the scams and viruses you may run into and how you can protect your computer.
Select a heading below to reveal more FAQs and expand to read more.
Security Terms: Defined
What is WEP Encryption?
WEP (Wired Equivalent Privacy) encryption is a security method that allows you to protect the data that is sent and received over the wireless connection between your modem router and computers. Encryption changes your data so that it is unreadable if “pulled out of the air” by a user who does not know the encryption key. However, when the authorized modem router or adapter receives data, it uses the encryption key to turn it back into readable data. Any other users attempting to connect to your network must know the encryption key to gain access to your network in the same way that you need a specific key to unlock the door to your house.
Most modem routers allow you to identify a WEP encryption key for your modem router to use. In some cases, you will be asked to specify a pass phrase that automatically generates the encryption key, a long string of letters and numbers. You then need to use this encryption key or pass phrase whenever you set up a wireless adapter to connect a computer wirelessly to your network. Other manufacturers preset a WEP encryption key for each modem router and specify this key on the modem itself. In the same way, you will need to use this encryption key when setting up your wireless adapters.
We recommend writing down your selected pass phrase or encryption key and keeping it in a safe place in case you want to add additional computers or adapters to your home network at a later time. AOL recommends you choose a pass phrase that contains 13 characters for 128-bit WEP encryption. This means you will still be able to connect your wireless adapters to your modem router, even if you use products from different manufacturers.
You may be asked to select the size of the encryption keys you wish to use: 64-bit or 128-bit. The larger the key, the more complex the encryption. Therefore, AOL recommends using 128-bit encryption.
Some routers also allow you set up an alternative type of encryption called WPA. However, not all of the adapters currently available support this type of encryption. AOL recommends that you use WEP encryption unless you are confident that all of your hardware supports WPA encryption.
What is a virus?
A virus is a program that causes damage to your computer either by deleting or corrupting files. A virus can also interfere with computer operations by multiplying itself to fill up disk space or random access memory space, secretly “infecting” your computer.
What is a worm?
A worm is a type of virus that spreads through your computer by creating duplicates of itself on other drives, systems and networks. One feature that makes worms so dangerous is that they can send copies of themselves to other computers across a network via email, an infected webpage, instant messages and Internet Relay Chat. One way to recognize a worm is if it has an "@m” or “@mm" designation, which signifies that the file’s primary distribution method is through email.
How can spyware affect me?
Spyware can harm your computer in several ways. It can secretly install software on your computer, change your browser homepage, reset your bookmarks and change your desktop wallpaper. But most importantly, spyware can invade your privacy by gathering your personal information and distributing it to others, making you susceptible to scams, identity theft and fraud. With spyware, strangers could use your credit card numbers and access your banking information, as well as your passwords and personal emails.
What is the difference between worms and Trojan horses?
A virus is a program that’s capable of continually replicating with little or no user intervention. There’s typically a piece of code that causes an unexpected and usually malicious event (or “payload”) to occur. Viruses are often disguised as games or images with clever, inviting titles such as "Pictures of ME".
A worm is a virus that spreads by creating duplicates of itself on other drives, systems or networks. Worms may send copies of themselves to other computers across network connections, through email, through an infected Web page or through instant messages and Internet Relay Chat (IRC). Some worms are differentiated as being "@m" or "@mm", which signifies that their primary distribution method is through electronic mail or mass-mail.
A Trojan horse is a program that either pretends to have, or is described as having, a set of useful or desirable features but actually contains a damaging payload. True Trojan horses are not technically viruses, since they do not replicate; however, many viruses and worms use Trojan horse tactics to initially infiltrate a system. Although Trojans are not technically viruses, they can be just as destructive. Many people use the term "Trojan" to refer only to non-replicating malicious programs, thus making a distinction between Trojans and viruses.
What is a virus hoax?
There are a lot of viruses out there; however, some aren't really out there at all. Virus hoaxes are more than mere annoyances. They may lead some users to routinely ignore all virus warning messages, leaving them vulnerable to a genuine, destructive virus. Next time you receive an urgent virus warning message be sure to check the list of known virus hoaxes. A common hoax is the Jdbgmgr.exe hoax . It describes an otherwise legitimate system file as being a virus that is not detected by McAfee or Norton. It hibernates in your computer system for 14 days before blowing your computer to smithereens. The file is displayed with a teddy bear icon and is often convincing as a result.
Remember to never open an email attachment unless you know what it is -- even if it's from someone you know and trust.
Common Hoax email Phrases:
- [email virus hoax name here], do not open it!
- Delete it immediately! It contains the [hoax name] virus.
- It will delete everything on your hard drive and [extreme and improbable danger specified here].
- This virus was announced today by [reputable organization name here].
- Forward this warning to everyone you know! (Remember that virus writers can use known hoaxes to their advantage. For example, AOL4FREE began as a hoax virus warning. Then somebody distributed a destructive Trojan attached to the original hoax virus warning.)
- Always remain vigilant.
- Never open a suspicious attachment.
What is spyware?
One of many Potentially Unwanted Programs (PUPs) is malicious software — also called malware — that downloads itself onto your computer through programs you download, emails you open or websites you visit. While spyware is not as damaging to a PC as a virus, it slows down your computer and tries to gather your personal information.
What are bots?
Bots are software applications that run automated tasks over the internet. There are several kinds of bots that can be used for helpful as well as destructive purposes. Scammers and hackers use spybots to grab website and email content to reuse without your permission. Internet bots can also be used to commit fraudulent activities, especially on computer gaming websites. Bots will take the form of viruses and worms, which can severely damage your computer and the information stored on it. To download anti-bot software, visit AOL Internet Security Central.
What is an IP Address?
An Internet Protocol address (IP address) is a unique number that is used to identify and communicate on a network utilizing the Internet Protocol standard.
If you need the IP address assigned to your computer by your Internet Service Provider (ISP) or by a Network service, please contact your ISP or Network Administrator.
What is anti-spyware?
If you’re constantly bombarded by pop-ups or you’ve noticed your computer suddenly seems slower and bogged down, you might need to download anti-spyware software.
Spyware not only can do serious harm to your computer, but can also invade your privacy. Spyware can steal your information by recording your key strokes when you enter your credit card number on Amazon.com, or by observing your computer screen during online banking. The worst case scenarios can lead to fraud and even identity theft.
Anti-spyware software protects your computer by identifying and removing spyware before it can do any damage. We recommend you follow the link to download AOL’s McAfee Internet Security Suite – Special Edition. Click Find Out More on the section of the McAfee box that best describes your relationship with AOL (paid member, free member or non-member) and then follow the on-screen instructions.
There are several other anti-spyware programs out there, too, including Ad-Aware SE Personal Edition and Spybot – Search & Destroy. These programs are not currently offered through AOL.
What is a Pup?
A Potentially Unwanted Program (PUP) is a piece of software that is usually created by a legitimate corporation for some sort of beneficial purpose. (Though, to whom it’s beneficial may be debatable.) So what’s the problem? PUPs can sometimes tamper with the security state of your computer if installed.
PUPs are broken down into six major categories including an “Other” category. Most PUPs behave similarly to Trojan horses; while, in some cases, the software isn’t designed to do any harm, it can easily be misused for more corruptive purposes.
The Six PUPs
- Adware
Adware is any software that, once installed on your computer, tracks your Internet browsing habits and sends you pop-ups containing advertisements related to the sites and topics you’ve visited. While this type of software may sound innocent, or even helpful, it consumes and slows down your computer’s valuable processor and Internet connection speed.
- Spyware
Spyware is similar to adware but much more personally invasive. After downloading itself onto your computer through another program you downloaded, an email you opened, or a website you visited, it scans your hard drive for personal information and your Internet browsing habits. Once the spyware finds your email address, it can send you spam and junk emails that clutter your inbox.
Spyware can be broken down into two categories:
- Advertising spyware: Gathers your personal information and/or shows pop-up advertisements. Even worse, it logs your personal information, including passwords, email addresses, browsing history, online buying habits, your computer’s hardware and software configurations and your name, age and sex.
- Surveillance spyware: Collects private information using key loggers that track keystrokes as well as instant message and chat sessions, collecting such private information as bank account and credit card numbers. This variety of spyware also includes Trojan horses, which can take control of your computer.
- Password Crackers
Software designed to allow you to recover lost or forgotten passwords from accounts or data files are called password crackers. They can be helpful to you as an innocent yet forgetful user, but when in less-honest hands these same useful tools allow access to confidential info and pose a serious privacy threat.
- Remote Administration Tools
This type of software is designed to allow remote control of a computer by a trusted and knowledgeable administrator, such as a tech support expert; however, when controlled by someone other than a legitimate owner or administrator, this software can pose a huge security risk.
- Dialers
Dialer software redirects Internet connections to another person’s computer, racking up additional connection charges for you and your Internet provider while providing free Internet access for the cyber thief.
- Jokes
Joke software has no malicious intent or use and doesn’t threaten your security or privacy — but it can be really annoying.
- Other
There are several random pieces of software out there, such as FTP servers, that also can be misused to help spread traditional malware.
Cookies are small text files used by many websites to store information about page visits and other settings, which is why a site might remember your username and the fact that you love, love, LOVE Elvis. While most cookies are harmless, some could inherently store personal information about you or track the pages you’ve visited and the ads you’ve clicked on so an advertiser can target your interests.
What about computer hardware issues?
Not All Computer Problems Are Virus Related. Nowadays, it’s easy to blame any computer problem on a virus. Listed below is a list of common problems NOT caused by a virus or other malicious code:
- Hardware problems. There are no viruses that can physically damage computer hardware, such as chips, boards and monitors.
- The computer beeps at startup with no screen display. This is usually caused by a hardware problem during the boot process. Check your computer documentation for the meaning of the beep codes.
- The computer does not register 640K of conventional memory. This can be a sign of a virus, but it is not conclusive. Some hardware drivers such as those for the monitor or SCSI card can use some of this memory. Consult with your computer manufacturer or hardware vendor to determine if this is the case.
- You have two antivirus programs installed and one of them reports a virus. While this could be a virus, it can also be caused by one antivirus program detecting the other program's signatures in memory.
- You are using Microsoft Word and it warns you that a document contains a macro. This does not mean that the macro is a virus.
- You are not able to open a particular document. This is not necessarily an indication of a virus. Try opening another document or a backup of the document in question. If other documents open correctly, the document may be damaged.
- The label on a hard drive has changed. Every disk is allowed to have a label. You can assign a label to a disk by using the DOS Label command.
Does my computer have any antivirus software?
Unsure if you have antivirus software? That’s a pretty easy fix. Choose from one of the strategies below to determine if you have antivirus software:
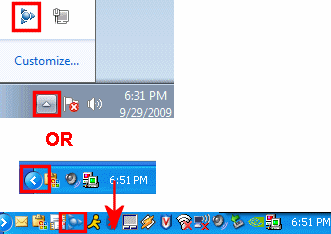
Search among the taskbar icons
On the Windows taskbar, hold your mouse over each icon next to the clock. The name of the program represented by the icon will appear. Read the name to determine whether the icon represents antivirus software.
Notes:
- If you are using Windows 7 and don't see all the icons, click the arrow next to the clock to reveal hidden icons
- If the program name does not indicate what the program is, double-click the icon to open the program. On the toolbar, click the Help menu, and then click About.
Search in Programs menu
- Click Start, and then click All Programs or Programs.
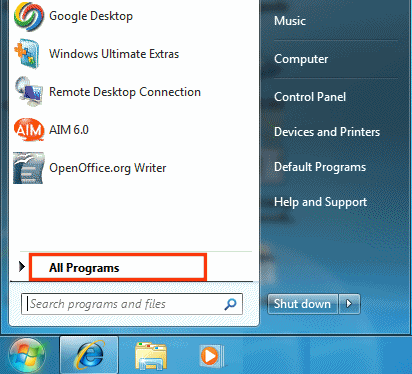
- Review the listed programs for antivirus software.
Search in Add/Remove Programs
Windows 7/Vista
- Click Start, and then click Control Panel.
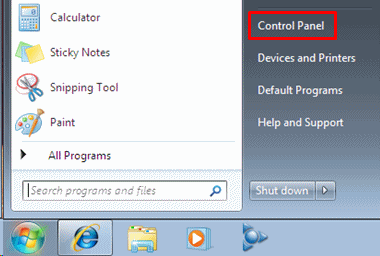
- Click Programs.
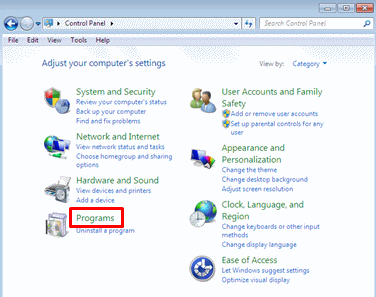
Note: If you can't find Programs, click Programs and Features, and then skip to Step 4.
- Click Uninstall a program.
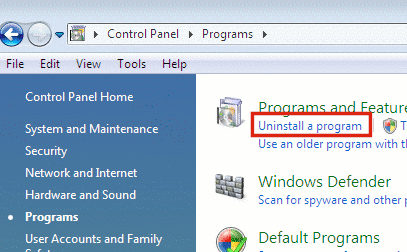
- Review the listed programs for antivirus software.
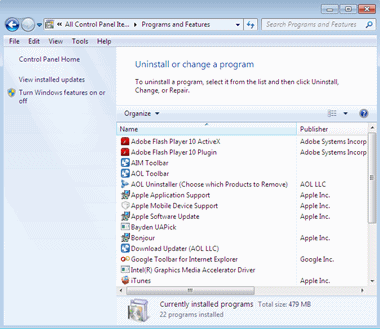
Windows XP/2000/Me/98
- Open the Control Panel.
- If you are using Windows XP, click Start, and then click Control Panel.
- If you are using Windows 2000/98/Me, click Start, select Settings, and then click Control Panel.
- Click Add or Remove Programs or the Add/Remove Programs icon.
- Review the Currently installed programs list for antivirus programs.
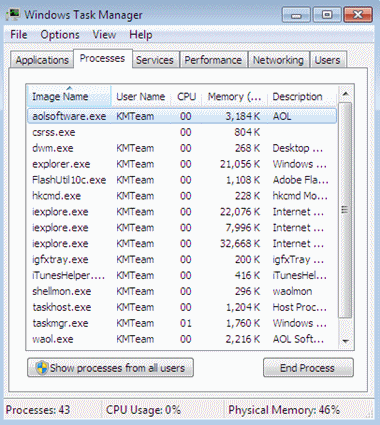
Search in Windows Task Manager
Windows 7/Vista/XP/2000
- Right-click a blank area on the Windows taskbar, and then click Start Task Manager or Task Manager.
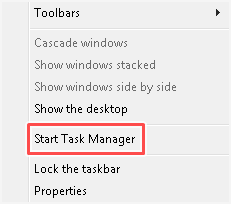
- Review the listed programs for antivirus software.
AOL System Information 2.0
- Open the AOL System Information window.
- If you are using Windows 7/Vista, click Start. In the Search box, type system. Make sure to highlight AOL System Information, and then press Enter. If prompted by the User Account Control window, click Yes or Continue.
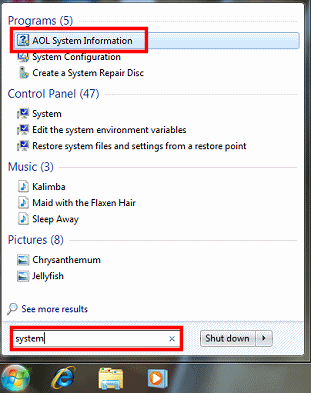
Note: If no window appears, check the Windows taskbar for a flashing tab. If you see the flashing tab, click it. The User Account Control window will now appear. Click Yes. Now, the AOL System Information window will appear.

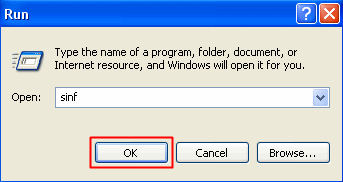
- If you are using Windows XP/2000/Me/98, click Start, and then click Run. In the Open box, type sinf, and then click OK. If prompted by a caution window, click OK.
- If you are using Windows 7/Vista, click Start. In the Search box, type system. Make sure to highlight AOL System Information, and then press Enter. If prompted by the User Account Control window, click Yes or Continue.
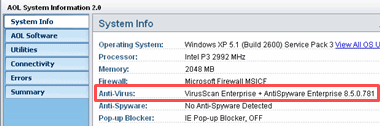
- Find the name of the antivirus software installed on your computer next to Anti-Virus in the System Info tab.
Windows Me/98
- Hold the Ctrl and Alt keys, and then tap the Delete key once.
Note: If you tap the Delete key twice while holding down the Ctrl and Alt keys, your computer will restart.
- Review the list of programs for antivirus software.
What to do if your computer has a virus
How could my computer get infected?
The most common ways your computer can get infected with spyware or other malware are by:
- Installing freeware or shareware
- Installing screen savers or games
- Downloading email attachments
- Clicking on a pop-up ad
- Visiting adult websites
- Not having antivirus software installed on your computer
How can I tell if my computer is infected by spyware?
The tell-tale signs that your computer is infected with spyware or other malware are:
- You receive annoying pop-up ads on a regular basis
- A mysterious new toolbar appears on your computer or browser
- Your PC noticeably slows down
- There are new, unfamiliar icons in your system tray
What do I do if my computer has a virus?
If your computer is infected with a computer virus, use antivirus software to detect and remove the malware.
If you don’t have antivirus software but you’re still able to connect to the internet, visit AOL Internet Security Central for information about computer safety, viruses and antivirus software.
If the virus is preventing you from getting online, contact your PC vendor to send you the necessary antivirus software.
How do I prevent spyware from infecting my computer?
- Start by running anti-spyware software on a regular basis to catch any programs that may have infected your computer. After the software removes the spyware it finds, restart your computer and scan it again to be safe, to make sure all spyware was deleted. Some spyware programs can be stubborn and difficult to remove, so it might take more than one try.
- Be careful when downloading free programs, especially music files and media sharing programs. Read the licensing agreements to understand exactly what you’re downloading. Many popular applications include spyware components, and some applications won’t work without those components.
- Protect your computer with a firewall, especially if you use a broadband connection.
- Use antivirus software to catch viruses, worms and Trojan horses before they can do any damage.
- Don’t download any programs from websites you don’t trust.
- Adjust your browser’s Internet Zone security settings to provide at least a medium level of security. A lower setting makes it easier for malware to access your computer.
- ActiveX controls are prone to spyware and other malware, so don’t approve the installation of any ActiveX controls you haven’t already requested.
Which spyware protection software should I install?
We recommend AOL’s own McAfee Internet Security Suite – Special Edition as well as Ad-Aware SE Personal Edition or Spybot – Search & Destroy.
About Firewalls
What is a firewall?
A firewall helps safeguard your computer or home network against unwanted, outside access. Properly configured firewalls can help protect your computer from hackers, worms, viruses, Trojan horses and other security attacks. These malicious programs may also use your computer to attack other computers. A firewall acts as a wall to block these programs and hackers from accessing your computer or home network. This is important for both dial-up and high-speed users since all computers connected to the internet are at risk of becoming a hacker’s target, especially if they do not have a firewall.
Hackers or malicious programs may try to access your computer or home network for a number of reasons, such as gathering personal or confidential information about you, accessing your Internet Service Provider (ISP) or copying private documents stored on your computer. Some hackers are simply looking for the challenge. It is important to keep any firewall software up to date since the methods used for bypassing firewalls change constantly.
Like any security system, no firewall is fail-safe, but when used in conjunction with other security measures such as antivirus software and good safety habits, a firewall provides enhanced protection every internet user should have. It’s important to remember that antivirus software is not a substitute for a firewall. Check out AOL Internet Security Central for more information about online safety and spotting scams/schemes.
Good online safety habits include:
- Downloading files only from trusted, known sources
- Never giving out personal information to sites you don’t trust
- Keeping Secure Passwords
How do firewalls work?
Most firewalls offer different levels of security that control the flow of traffic from the internet to your computer. For example, a firewall can allow all traffic, allow only the traffic that you designate as trusted or block all traffic to your office or home network. The firewall does this by monitoring the programs on your computer that access the internet. Your preferences designate the security level of your firewall.
What are the different types of firewalls?
Firewalls come in a variety of forms and provide varying levels of customization, features and updates. They may vary from hardware devices such as routers to software programs that you load onto your PC, or may even be bundled with your computer's operating system. These firewalls range in price and may be free downloads, one-time purchases or subscription services. Some common firewall options are:
- Software firewalls: Many vendors, such as McAfee, Symantec and Zone Labs, offer free or premium firewall software that you can download from their websites or purchase at retail locations. Software firewalls require security updates from the vendor to maintain their effectiveness. Setting your firewall preferences to auto-update will increase the firewall's security capabilities.
- Router or gateway-based firewalls: Many broadband home networking routers (or gateways) include a built-in firewall as a basic feature. A router-based firewall can help protect all of the computers on your network by preventing unwanted traffic from traveling through the router and being sent to the computers.
- Operating system firewall support: Examples of this type of firewall can be found in Microsoft Windows XP or Macintosh OS X. These firewalls are embedded in the operating system and may need to be turned on.
How do I choose a firewall?
If you are setting up a home network, you should purchase a router or gateway that has a firewall as a standard feature. Some people with a router-based firewall also prefer the added security of a software firewall for each of their connected computers. If you don’t have a home network or a router with built-in firewall protection, AOL offers the McAfee Internet Security Suite.
How do I use firewalls with game consoles?
PS2 users may experience problems connecting their game console behind a firewall. The easiest way to avoid a firewall conflict is to connect your game console's network adapter directly via Ethernet to your cable or DSL modem.
Note:You may still experience problems in connecting to specific game servers or hosting online games.
Programs that request internet access
Why do programs request internet access?
A program (for example, explorer.exe, rundll.exe, or svchost.exe) might be called by another program to communicate with the internet. Some of the other reasons why a program might request internet access is to:
- Check for automatic updates
- Retrieve information such as email, news or music
- Communicate with a licensing server to verify your right to use the program
- Communicate with a server to submit your registration information
Why do programs request server access?
A program might request server access if it expects to receive anonymous connections from the internet. Examples of this include some online games, messenger applications and file-sharing applications. You should only allow an application server access if you recognize and trust the application and if you want it to be able to receive anonymous connections.